An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
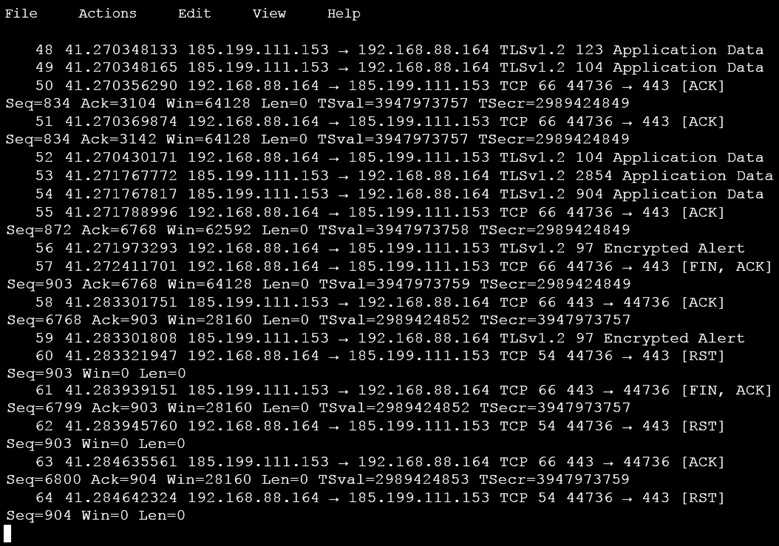
Which obfuscation technique is the attacker using?
- Base64 encoding
- TLS encryption
- SHA-256 hashing
- ROT13 encryption
Answer(s): B
Explanation:
ROT13 is considered weak encryption and is not used with TLS (HTTPS:443).
Reference:
https://en.wikipedia.org/wiki/ROT13