ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead. ARP spoofing attack is used as an opening for other attacks.
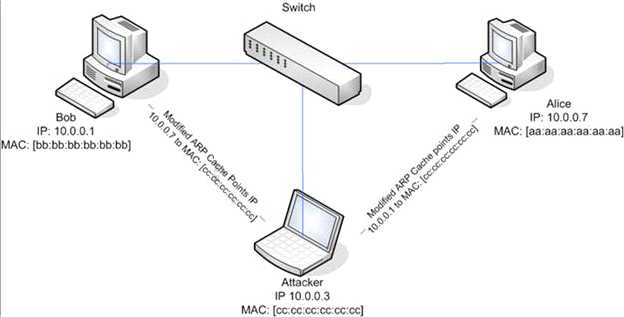
What type of attack would you launch after successfully deploying ARP spoofing?
- Parameter Filtering
- Social Engineering
- Input Validation
- Session Hijacking