Refer to the exhibits.
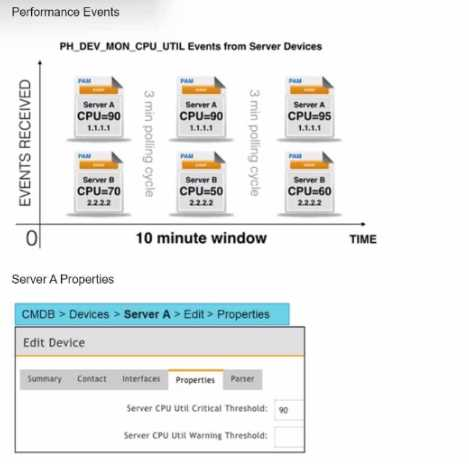
Three events are collected over a 10-minute time period from two servers: Server A and Server B. Based on the settings tor the rule subpattern. how many incidents will the servers generate?
- Server A will generate one incident and Server B will generate one incident.
- Server A will generate one incident and Server B will not generate any incidents.
- Server B will generate one incident and Server A will not generate any incidents.
- Server A will not generate any incidents and Server B will not generate any incidents.
Answer(s): D
Explanation:
Event Collection Overview: The exhibits show three events collected over a 10-minute period from two servers, Server A and Server B.
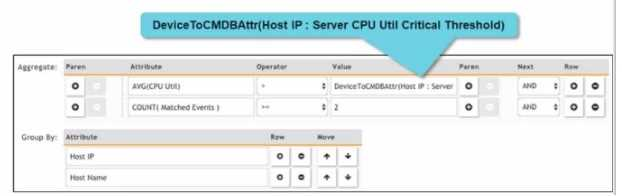
Rule Subpattern Settings: The rule subpattern specifies two conditions:
AVG(CPU Util) > DeviceToCMDBAttr(Host IP : Server CPU Util Critical Threshold): This checks if the average CPU utilization exceeds the critical threshold defined for each server. COUNT(Matched Events) >= 2: This requires at least two matching events within the specified period.
Server A Analysis:
Events: Three events (CPU=90, CPU=90, CPU=95).
Average CPU Utilization: (90+90+95)/3 = 91.67, which exceeds the critical threshold of 90. Matched Events Count: 3, which meets the condition of being greater than or equal to 2. Incident Generation: Server A meets both conditions, so it generates one incident.
Server B Analysis:
Events: Three events (CPU=70, CPU=50, CPU=60).
Average CPU Utilization: (70+50+60)/3 = 60, which does not exceed the critical threshold of 90. Matched Events Count: 3, but since the average CPU utilization condition is not met, no incident is generated.
Conclusion: Based on the rule subpattern, Server A will generate one incident, and Server B will not generate any incidents.
Reference:
FortiSIEM 6.3 User Guide, Event Correlation Rules and Incident Management sections, which explain how incidents are generated based on rule subpatterns and event conditions.