HOTSPOT (Drag and Drop is not supported).
You have a Microsoft 365 E5 tenant that connects to Microsoft Defender for Endpoint. You have devices enrolled in Microsoft Intune as shown in the following table.
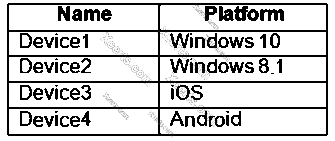
You plan to use risk levels in Microsoft Defender for Endpoint to identify whether a device is compliant. Noncompliant devices must be blocked from accessing corporate resources.
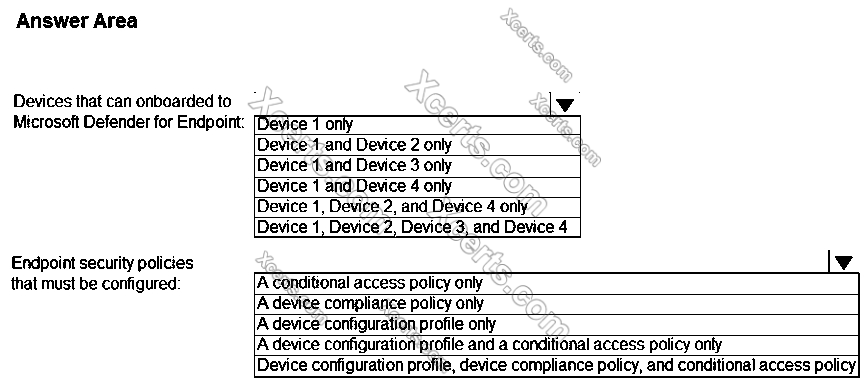
You need to identify which devices can be onboarded to Microsoft Defender for Endpoint, and which Endpoint security policies must be con gured.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
- See Explanation section for answer.
Answer(s): A
Explanation:
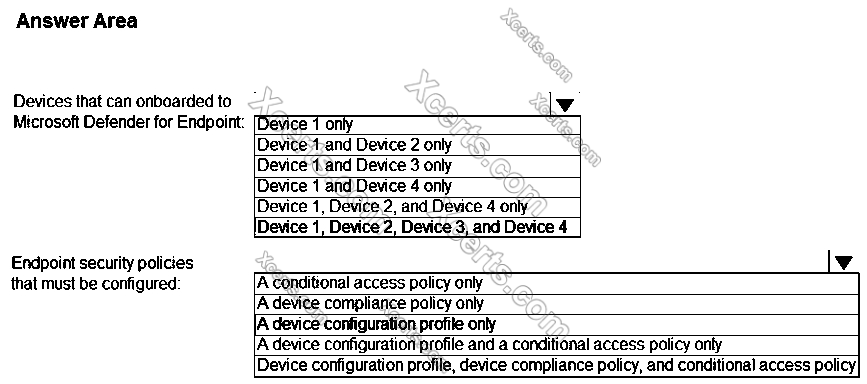
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/con gure-machines-onboarding?view=o365-worldwide