Refer to the exhibit.
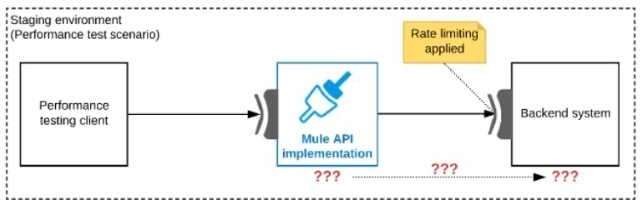
One of the backend systems invoked by an API implementation enforces rate limits on the number of requests a particular client can make. Both the backend system and the API implementation are deployed to several non-production environments in addition to production.
Rate limiting of the backend system applies to all non-production environments. The production environment, however, does NOT have any rate limiting.
What is the most effective approach to conduct performance tests of the API implementation in a staging (non-production) environment?
- Create a mocking service that replicates the backend system's production performance characteristics. Then configure the API implementation to use the mocking service and conduct the performance tests
- Use MUnit to simulate standard responses from the backend system then conduct performance tests to identify other bottlenecks in the system
- Include logic within the API implementation that bypasses invocations of the backend system in a performance test situation. Instead invoking local stubs that replicate typical backend system responses then conduct performance tests using this API Implementation
- Conduct scaled-down performance tests in the staging environment against the rate limited backend system then upscale performance results to full production scale
Answer(s): A
Explanation:
Correct answer is Create a mocking service that replicates the backend system’s production performance characteristics. Then configure the API implementation to use the mocking service and conduct the performance tests
* MUnit is for only Unit and integration testing for APIs and Mule apps. Not for performance Testing, even if it has the ability to Mock the backend.
* Bypassing the backend invocation defeats the whole purpose of performance testing. Hence it is not a valid answer.
* Scaled down performance tests cant be relied upon as performance of API's is not linear against load.