The following excerpt is taken from a honeyput log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. Study the log given below and answer the following questions:
(Note: The objective of this question is to test whether the student has learnt about
passive OS fingerprinting (which should tell them the OS from log captures): can they tell a SQL injection attack signature; can they infer if a user ID has been created by an attacker and whether they can read plain source – destination entries from log entries.)
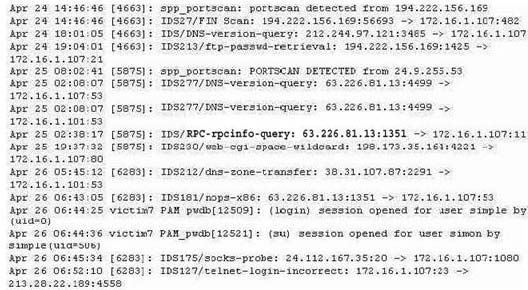
What can you infer from the above log?
- The system is a windows system which is being scanned unsuccessfully.
- The system is a web application server compromised through SQL injection.
- The system has been compromised and backdoored by the attacker.
- The actual IP of the successful attacker is 24.9.255.53.