A customer is evaluating device profiles on a CX 6300 switch. The test device has the following attribute:
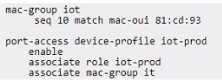
· MAC address=81:cd:93:13:ab:31
The test device needs to be assigned the "lot-prod'' role, in addition the "lot-default" role must be applied for any other device connected lo interface 1/1/1. This is a lab environment with no configuration of any external authentication server for the test. Given the configuration example, what is required to meet this testing requirement?
- Enter the command "pot-access device-profile mode block-until-profile-applied"" for interface 1/1/1.
- Enter the command "port-access fallback-role lot-default globally
- Enter the command "port-access onboarding-method precedence" to set device profiles with a lower precedence.
- Enter the command "port-access device-profile mode block-until-profile-applied" globally.
Answer(s): B
Explanation:
The fallback role is used as a default role in the absence of a specified role or when an authentication server is not available. Given the scenario, where the test device with MAC address 81:cd:93:13:ab:31 needs to be assigned to "iot-prod" and other devices to "iot-default", and considering there is no external authentication server configured for the test, the appropriate action would be to set a global fallback role that applies to all devices connecting to the network. This ensures that any device that does not match the specific device profile will inherit the "iot-default" role. Since the configuration for a specific MAC address (81:cd:93:xx:xx:xx) to associate with the "iot- prod" role is already in place, setting the fallback role globally accommodates the requirement for other devices.