HOTSPOT (Drag and Drop is not supported)
You have an Active Directory Domain Services (AD DS) domain that contains 1,000 users.
The domain has the following password requirements:
The minimum password length must be 12 characters.
Passwords must expire in 90 days.
Passwords must be complex.
You need to ensure that the members of a security team have passwords that meet the following requirements:
The minimum password length must be 16 characters.
Passwords must expire in 60 days.
Passwords must be complex.
The solution must minimize the impact on users who are NOT members of the security team.
What should you do? To answer, select the appropriate options in the answer area.
Note: Each correct selection is worth one point.
Hot Area:
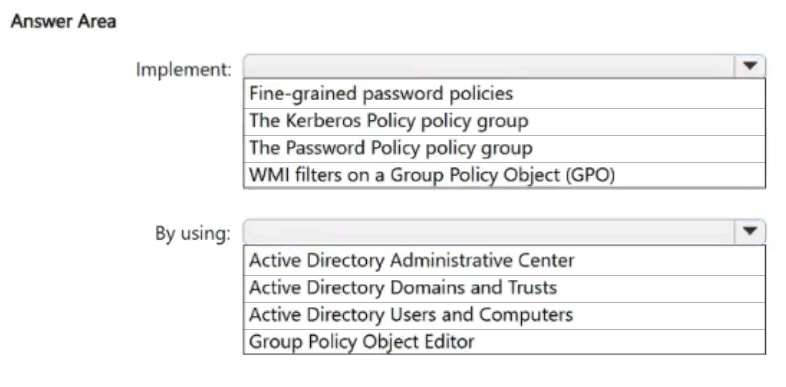
- See Explanation section for answer.
Answer(s): A
Explanation:

Box 1: Fine Grained Password Policies
Implement
Configure fine grained password policies for Active Directory Domain Services Fine Grained Password Policies provide you with a way to define different password and account lockout policies for different sets of users in a domain. You can use fine grained password policies to specify multiple password policies within a single domain. You can also apply different restrictions for password and account lockout policies to different sets of users in a domain. For example, you can apply stricter settings to privileged accounts and less strict settings to the accounts of other users.
Fine-grained password policies apply only to global security groups and user objects. By default, only members of the Domain Admins group can set fine grained password policies. However, you can also delegate the ability to set these policies to other users.
Box 2: Active Directory Administrative Center
By using
Create a fine grained password policy
Here's how to create a fine grained password policy using ADAC:
-> 1. Open Active Directory Administrative Center, either from the Tools menu of the Server Manager console or by running an elevated PowerShell session and typing dsac.exe.
2. If the appropriate target domain isn't selected, choose Manage, choose Add Navigation Nodes, and select the appropriate target domain in the Add Navigation Nodes dialog box and then choose OK.
3. In the ADAC navigation pane, open the System container, and then choose Password Settings Container.
4. In the Tasks pane, choose New, and then choose Password Settings.
5. Fill in or edit fields inside the property page to create a new Password Settings object. The Name and Precedence fields are required.
6. Under Directly Applies To, choose Add, type the name of the group to which the fine grained password policy, and then choose OK.
7. Choose OK to submit the creation.
Reference:
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/get-started/adac/fine-grained-password-policies